oracle 12c等待事件: Failed Logon Delay
Failed Logon Delay
昨天看到一份Oracle 12C R2的AWR top event是”Failed Logon Delay”, 发现12c 在安全方面又有几个参数的变化,简单的记录一下。
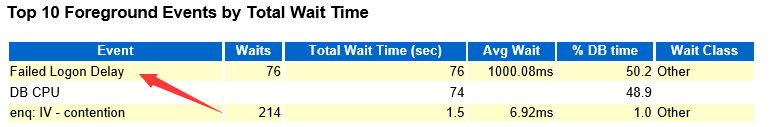
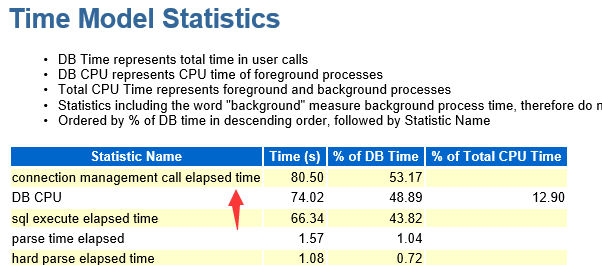
这个等待事件常常是因为有程序尝试使用错误的用户密码登录数据库, 如暴力破解程序.
这是一个安全特性用于控制延迟失败的登录,在oracle 11g版本是引入,但是在11g时常因为这个特性带来性能 问题,需要用event 28401 禁用密码延迟认证的特性。 控制认证失败尝试特性是有 sec_max_failed_login_attempts 和sec_protocol_error_further_Action 参数控制,但是在oracle 12c后对于以上参数值有了新的变化, sec_max_failed_login_attempts尝试失败次数(多个用户)11G是10次,在12ck中减少为3, 所以延迟的登录会更多, 这个参数不同于user profile中的失效次数主要是单个用户失败和多个用户失败。 sec_protocol_error_further_Action 这个参数控制失败后的处理方式,在11g时是CONTINUE 也就是可以继续,但是在12c 中默认改变为(DROP, 3), 为了系统稳定牺牲一个连接。
解决方法就是找错误尝试的主机,修正密码后即可。
查找方法可以使用audit
如 SQL>audit session whenever not successful;
查询aud$
或使用登录trigger(Note:可能会有一点点登录性能影响(<1%),找到源头后可以删除)
CREATE OR REPLACE TRIGGER logon_denied_to_alert
AFTER servererror ON DATABASE
DECLARE
-- author: anbob.com
-- purpose: print logon fail to db alert due to passwd wrong
message VARCHAR2(168);
ip VARCHAR2(15);
v_os_user VARCHAR2(80);
v_db_user varchar2(50);
v_module VARCHAR2(50);
v_action VARCHAR2(50);
v_pid VARCHAR2(10);
v_sid NUMBER;
v_program VARCHAR2(48);
BEGIN
IF (ora_is_servererror(1017)) THEN
-- get ip FOR remote connections :
IF upper(sys_context('userenv', 'network_protocol')) = 'TCP' THEN
ip := sys_context('userenv', 'ip_address');
END IF;
SELECT sid INTO v_sid FROM sys.v_$mystat WHERE rownum < 2;
SELECT p.spid, v.program
INTO v_pid, v_program
FROM v$process p, v$session v
WHERE p.addr = v.paddr
AND v.sid = v_sid;
v_os_user := sys_context('userenv', 'os_user');
v_db_user := sys_context('userenv', 'SESSION_USER');
dbms_application_info.read_module(v_module, v_action);
message := to_char(SYSDATE, 'YYYYMMDD HH24MISS') ||
' logon denied from ' || nvl(ip, 'localhost') || ' OSPid:' ||
v_pid || ' OS User:' || v_os_user || ' DB User:' || v_db_user ||' with ' || v_program || ' – ' ||
v_module || ' ' || v_action;
sys.dbms_system.ksdwrt(2, message);
END IF;
END;
/
_sys_logon_delay
另外对于12c中引入的对于SYS用户的尝试失败登录后的延迟是有参数新的参数”_sys_logon_delay“控制的,默认为1秒,加大参数可以防止非法尝试,配置值为0 可以禁用该特性。
MORE
SEC_MAX_FAILED LOGIN_ATTEMPTS is a new feature in Oracle 11g. It specifies the number of authentication attempts that can be made by a client on a connection to the server process. This parameter target against brute force attacks. An intruder could start a server process first and then try to establish connection by guessing/Program generated password. Using that parameter it is possible to limit the number of failed login attempts. After the specified number of authentication attempts fails, the database processes drop the connection. This initialization parameter is designed to stop intruder from attacking application, it does not apply to valid user. It is not a dynamic parameter.
SEC_MAX_FAILED_LOGIN_ATTEMPTS only works application uses OCI Program. It does not work in sqlplus so a user can try unlimited time with guessing password from sqlplus even though the parameter is set but usually intruder attack using OCI program.

 微信扫一扫,打赏作者吧~
微信扫一扫,打赏作者吧~


对不起,这篇文章暂时关闭评论。